Managing Access Policies
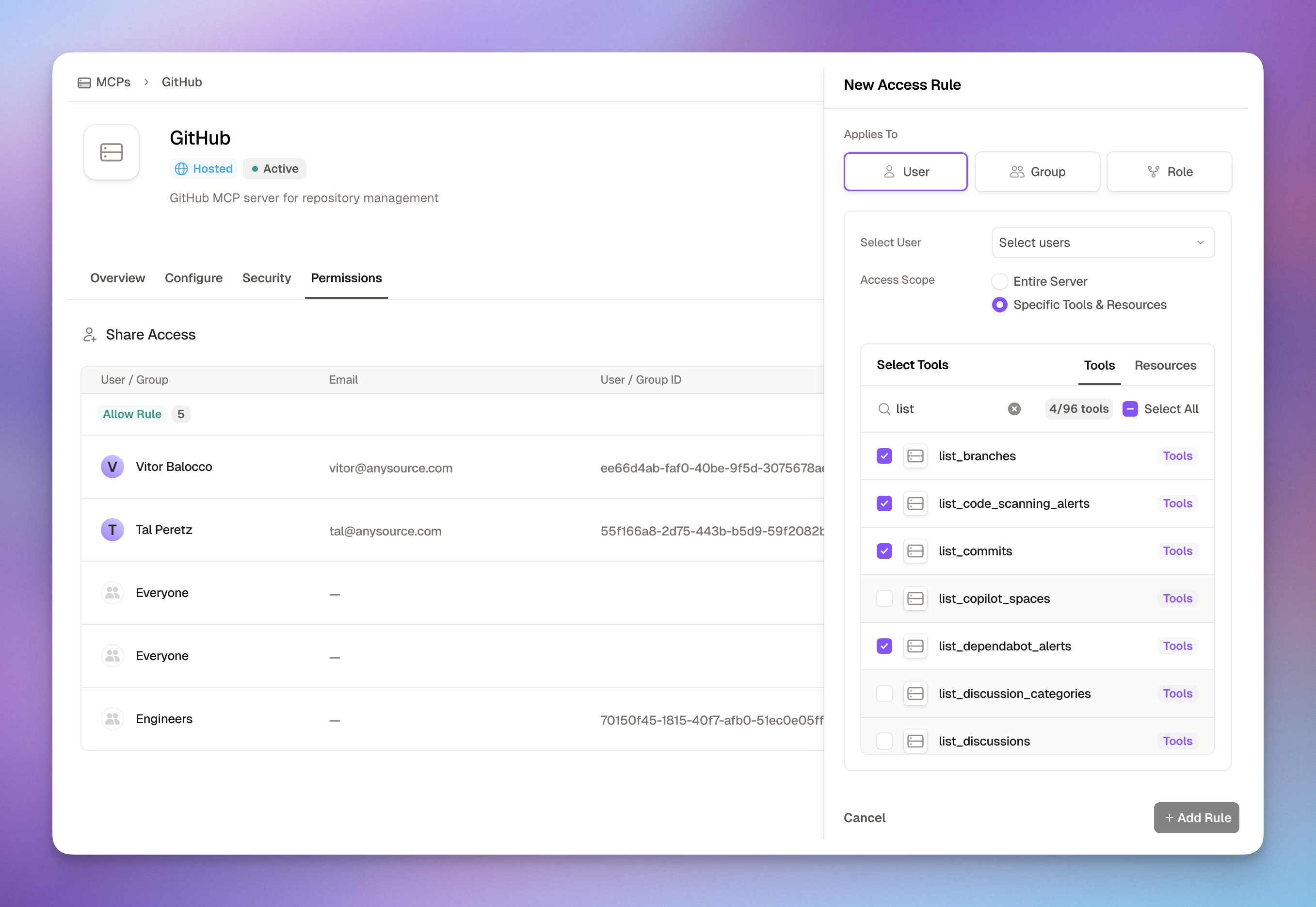
How Access Rules Work
Access rules grant permissions to users, groups, or roles for specific MCP servers: Applies To (Who gets access):- User: Individual employees by email/ID
- Group: Teams synced from your SSO (Engineering, Marketing, etc.)
- Role: Job functions or custom roles
- Entire Server: Full access to all tools in the MCP
- Specific Tools & Resources: Fine-grained selection of individual tools
- Add runtime rules based on tool arguments (e.g., restrict SQL queries to specific tables)
- Enforce network restrictions (e.g., corporate IP ranges only)
- Validate OAuth session properties (e.g., require verified accounts)
- Block specific MCP clients
Policy Types
Anysource supports two types of policies:Server-Level Policies
Manage access to specific MCP servers. Navigate to MCPs → [Server Name] → Policies tab.- Scope: One or more specific servers
- Action: Allow or Deny
- Use for: Granting access, fine-grained tool restrictions
- Example: Allow Finance group to use database query tools
Global Policies
Organization-wide restrictions that apply everywhere. Navigate to Admin → Policies.- Scope: All servers, tools, and resources (*)
- Action: Deny only
- Use for: IP blocks, client restrictions, compliance requirements
- Example: Block all access from outside corporate network
Creating Access Rules
Define Access Scope
Choose between:
- Entire Server: Grant access to all tools (faster, simpler)
- Specific Tools & Resources: Select individual tools (more secure, granular)
Access Rule Examples
Team-Wide Server Access
Scenario: Give all engineers access to the GitHub MCP- Teams need comprehensive access
- Server tools are all appropriate for the group
- Simplicity is preferred over granularity
Fine-Grained Tool Access
Scenario: Give finance analysts read-only access to the Database MCP- Sensitive MCPs require least privilege
- Only specific tools are needed
- Different roles need different capabilities
Individual User Access
Scenario: Give a contractor temporary access to specific Slack tools- Individual exceptions needed
- Temporary access for specific users
- Contractors or external collaborators
- Testing new MCPs with a single user first
Conditional Access by Tool Arguments
Scenario: Allow finance team to query only sales and finance tables- Database access needs table-level restrictions
- File systems need path-based access control
- APIs need parameter validation
- Sensitive data requires fine-grained control
Global Policy: Block External IPs
Scenario: Require all users to access MCPs from corporate network- Compliance requires network-based access control
- Remote work must use VPN
- Sensitive data needs IP restrictions
- Organization-wide security policy
Restrict Gmail to Internal Recipients Only
Scenario: Prevent outgoing Gmail messages to external recipients, allowing only emails sent to your internal domain (e.g.,@runlayer.com)
- Prevent data exfiltration via email in AI agent workflows
- Enforce internal-only communication for sandbox or development environments
- Provide guardrails for agents with Gmail access
- Meet compliance requirements for regulated data
- Test new AI workflows safely before allowing external communication
Best Practices
Start with Specific Tools, Not Entire Server
Start with Specific Tools, Not Entire Server
When in doubt, grant access to specific tools first. You can always expand later if needed.Why?
- Easier to add permissions than remove them
- Users won’t miss tools they didn’t know existed
- Reduces attack surface if credentials are compromised
Use Groups, Not Individual Users
Use Groups, Not Individual Users
Create access rules for groups whenever possible, even if the group only has one member initially.Why?
- Scales better as teams grow
- Easier to audit (who’s in “Engineering” vs 50 individual rules)
- Syncs automatically with SSO changes
- Simplifies onboarding/offboarding
Leverage SCIM for Automatic Group Sync
Leverage SCIM for Automatic Group Sync
Runlayer automatically syncs groups from your identity provider (IDP) via SCIM, mirroring your org structure.What this means:
- Groups from Okta, Azure AD, or Google Workspace sync automatically
- New employees added to groups get access immediately
- Employees removed from groups lose access instantly
- No manual group management needed
- Create access rules using your existing IDP groups
- Engineering, Sales, Finance groups work out of the box
- Changes in your IDP reflect in Runlayer instantly
Regularly Audit Access
Regularly Audit Access
Review access rules quarterly:
- Who has access to sensitive MCPs?
- Are there users who no longer need access?
- Can we tighten tool permissions?
- Prevents scope creep
- Maintains least privilege
- Required for compliance
Use Conditions for Fine-Grained Control
Use Conditions for Fine-Grained Control
Add conditions when scope alone isn’t enough:Good use cases:
- Restrict database queries to specific tables
- Limit file access to certain paths
- Validate API parameters
- Enforce network restrictions
payload.*- Tool arguments (e.g.,payload.table,payload.path)meta.request.ip- Client IP addressmeta.request.user_agent- HTTP User-Agent header for client identificationmeta.subject.*- Subject email, roles, groups, type (user or agent)meta.user.*- Alias formeta.subject.*(backward compatibility)meta.oauth.*- OAuth provider, scopes, verificationmeta.server.*- Server name, deployment mode, auth type
Use Global Policies for Organization-Wide Rules
Use Global Policies for Organization-Wide Rules
Apply security controls across all resources:Common use cases:
- Block access from outside corporate network
- Restrict access to approved clients only (e.g., allow only Cursor)
- Require OAuth verification
- Enforce compliance requirements
- Global policies can only DENY (not allow)
- They apply to all servers, tools, and resources
- Manage them in Admin → Policies
- Test with small groups before applying to everyone