This guide requires Jamf Pro. Jamf Now and Jamf School have different script deployment capabilities.
Prerequisites
- Jamf Pro admin access
- Configured enrollment key from Runlayer (see below)
- Devices enrolled via User-Approved MDM or Automated Device Enrollment (for Full Disk Access)
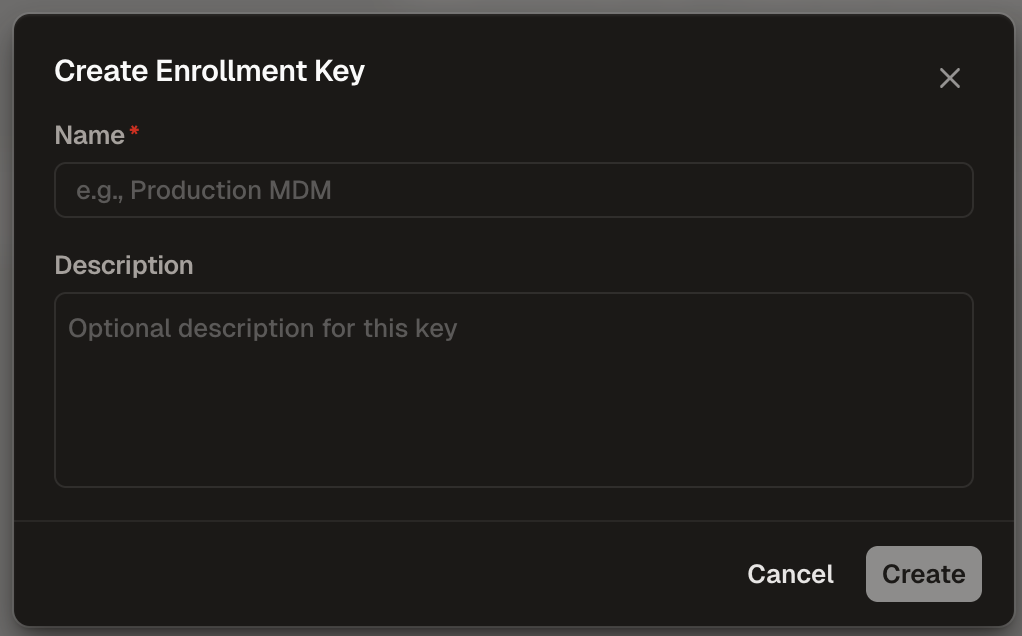
Creating an Enrollment Key
Creating an Enrollment Key
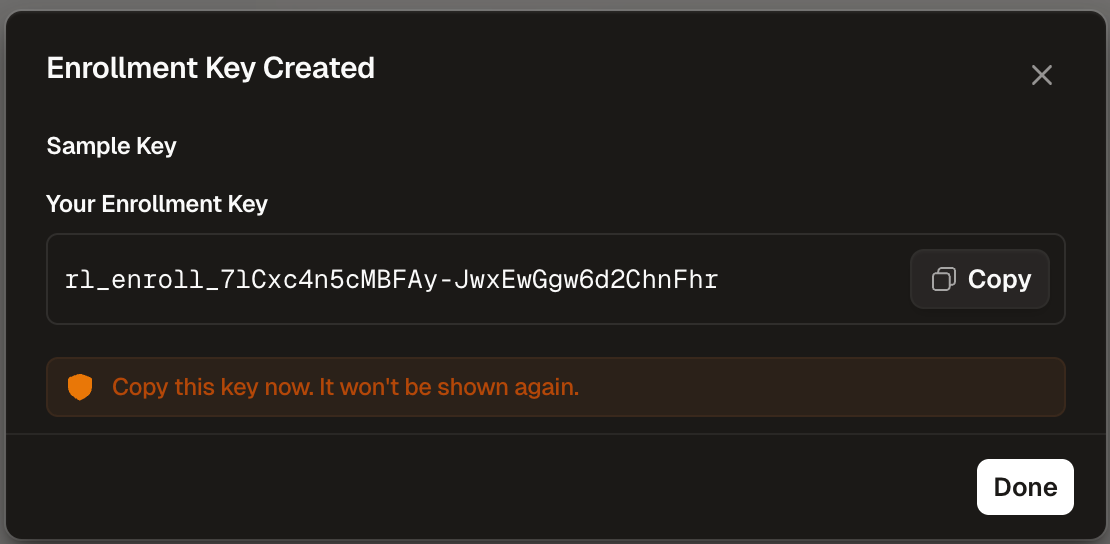
Enrollment keys allow devices to automatically register with Runlayer and obtain API credentials.

Navigate to Enrollment Keys
Go to Settings in the Runlayer dashboard and select the Enrollment Keys tab
Configure the Key
- Name (required): Enter a descriptive name (e.g., “Production MDM”)
- Description (optional): Add context about the key’s purpose
Deployment Steps
Deploy PPPC Profile
The PPPC profile grants Full Disk Access to the Runlayer scan wrapper binary (Option A: Use Jamf’s Built-in PPPC Configuration
/usr/local/bin/runlayer-scan). This wrapper is a signed macOS binary that spawns the scan process, which inherits FDA permissions. This scoped approach ensures only Runlayer scans receive FDA, not all uvx executions.The deployment script embeds the wrapper binary and installs it automatically. You only need to deploy this PPPC profile to grant it Full Disk Access.
- Navigate to Computers > Configuration Profiles
- Click New
- Give it a name (e.g., “Runlayer MCP Watch - Full Disk Access”)
- Under Privacy Preferences Policy Control, click Configure
- Add a single entry for the wrapper binary:
- Identifier:
/usr/local/bin/runlayer-scan - Identifier Type: Path
- Code Requirement:
identifier "com.runlayer.scan" - App or Service: SystemPolicyAllFiles, Access: Allow
- App or Service: SystemPolicyAppData, Access: Allow
- App or Service: SystemPolicyMediaLibrary, Access: Allow
- App or Service: Photos, Access: Allow
- App or Service: SystemPolicyDesktopFolder, Access: Allow
- App or Service: SystemPolicyDocumentsFolder, Access: Allow
- App or Service: SystemPolicyDownloadsFolder, Access: Allow
- App or Service: SystemPolicyNetworkVolumes, Access: Allow
- App or Service: SystemPolicyRemovableVolumes, Access: Allow
- Identifier:
- Scope to target computers/groups
- Save and deploy
PPPC Profile (runlayer-mcp-watch-profile.mobileconfig)
PPPC Profile (runlayer-mcp-watch-profile.mobileconfig)
Generate the Script
Fill in your organization’s settings below to generate a customized deployment script.Jamf-specific configuration tips:
ENROLLMENT_USERNAME: Use a Jamf variable or extension attribute that provides the user’s identity. Common variables:$EMAIL, or a custom extension attribute.ENROLLMENT_DEVICE_NAME: Use a Jamf variable or extension attribute that identifies the device. Common variables:$COMPUTERNAME,$SERIALNUMBER, or a custom extension attribute.
Upload to Jamf Pro
- Navigate to Settings > Computer Management > Scripts
- Click New
- Enter a display name (e.g., “Runlayer MCP Watch”)
- Paste the generated script contents
- Set Priority to “After” (runs after other policies)
- Save
Create a Policy
- Navigate to Computers > Policies
- Click New
- Configure the policy:
- General: Name it (e.g., “Deploy MCP Watch”)
- Scripts: Add your uploaded script
- Scope: Select target computers or groups
- Trigger: Choose execution trigger:
- Recurring Check-in: For periodic scans
- Login: Run when users log in
- Enrollment Complete: Run on new device enrollment
- Frequency: Set to Ongoing for repeated execution
Verification
Log Locations
| Platform | Log Location |
|---|---|
| macOS | /var/log/mcp-watch.log |
Exit Codes
| Code | Meaning |
|---|---|
| 0 | Success |
| 1 | General failure (missing config, enrollment failed) |
| 2 | Network failure |
| 3 | Installation failure |